Whether it’s physical, virtual, or in the cloud, discovering and blocking sophisticated threats in the network is at the forefront…


Whether it’s physical, virtual, or in the cloud, discovering and blocking sophisticated threats in the network is at the forefront…

Microsoft’s M12 has recently announced the launch of the Female Founders Competition, a startup initiative aimed at rewarding startup companies…

Workforce management (WFM) software is an all-encompassing term for mobile and desktop programs that are created to support a business…

The increasingly digitalized world we live in has a lot of benefits in business and in relationships, but with it…

If you are connected to the internet, then you are a target for malware, viruses, and hackers. Every day, 350,000…
What Do We Know About Terminal Fault (L1TF) Chip Vulnerabilities? Understanding The L1 Terminal Fault (L1TF) Intel has recently confirmed…
Azure Stack has commanded plenty of loyal followers since its release, and it’s easy to see why. The platform provides…

Is It Safe For Me To Use The Airport’s Public Wi-Fi When I Travel? Most airports around the U.S. and…

What Are The New Updates On Microsoft Office 365 For August 2018? As Microsoft continually works on improving the Office…

What Are The 10 Top Laptops of 2018? One does not just walk into a store and purchase the first…

Using Rules To Organize Your Outlook 2016 Inbox The purpose of Rules in Microsoft Outlook is to help you organize…
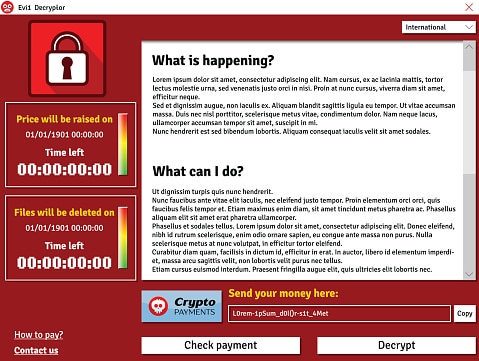
The Newest Forms Of Ransomware & How To Protect Your Business From Them The Situation Ransomware is now one of…